Unsupported and Unpatched
Article By : Ann R. Thryft

Vulnerable to attack, older Windows systems present modern challenges to OT network managers.
Many generations of older Windows systems are still widely used in industrial Internet of things (IIoT) and industrial control system (ICS) installations. The fact that Windows 7 reached end-of-life last month only broadens the already-vulnerable attack surfaces of IIoT and ICS networks and gives hackers even greater opportunity to infect them with malware and disrupt operations.
They’ve already started. Earlier this month, TrapX Security found a new malware campaign targeting IoT devices running embedded Windows 7 at several global manufacturing sites. The malware uses a self-spreading downloader to run malicious scripts. These can interfere with the operation of targeted devices such as automated guided vehicles, making them malfunction and cause damage. The TrapX report said the campaign is based on cryptocurrency miner Lemon_Duck PowerShell, discovered in enterprise networks last October. IoT devices from third parties that are already infected can easily enter an operational technology (OT) network undetected.
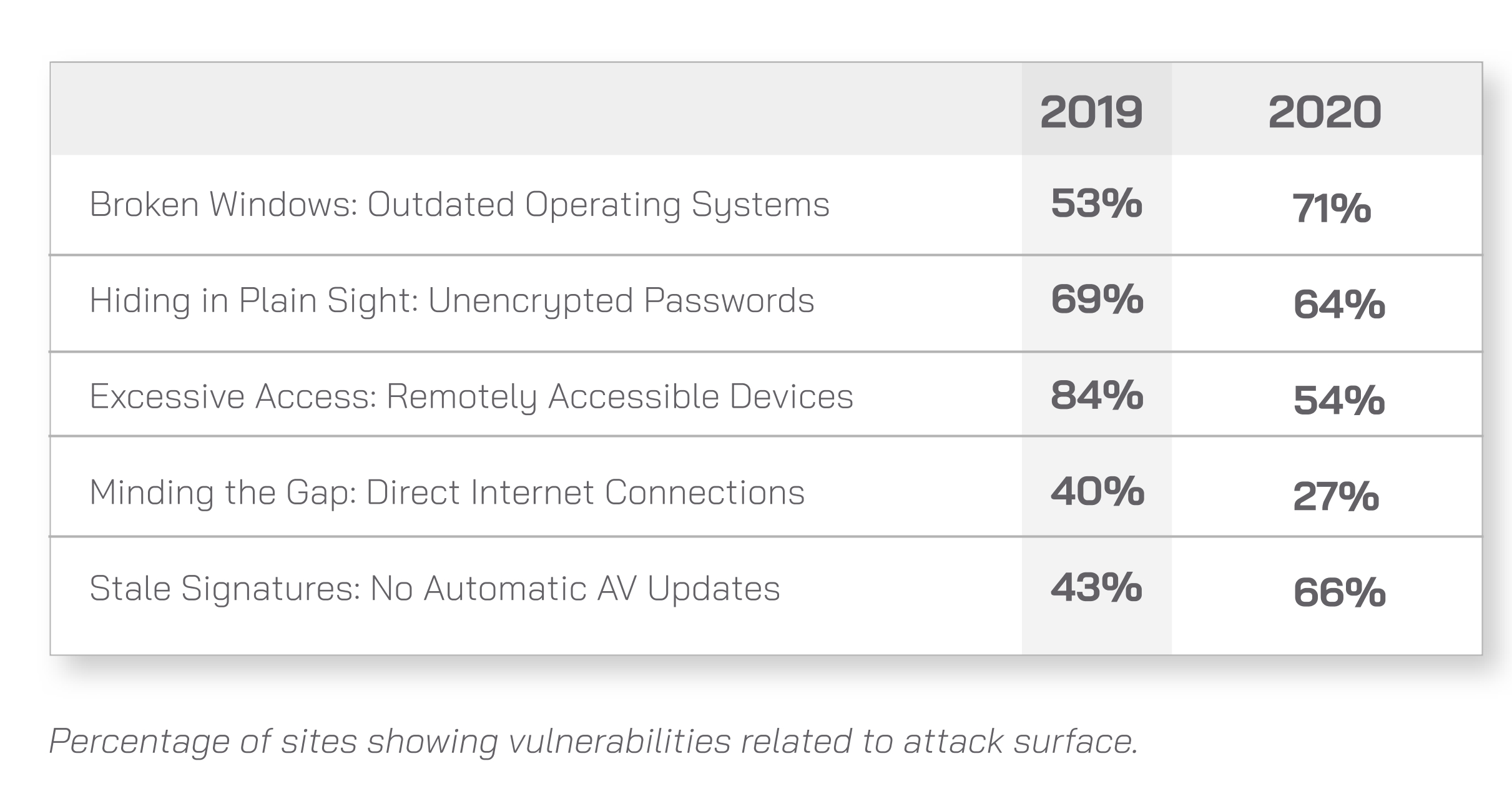
These vulnerabilities are not a small problem. According to the 2020 Global ICS and IIoT Risk Report by OT security firm CyberX, unsupported, unpatched, and unprotected Windows operating systems including Windows XP, 2,000, and now 7 account for 71% of sites examined. The report analyzed real-world traffic from more than 1,800 production IIoT/ICS networks in multiple sectors including energy utilities, oil and gas, manufacturing, pharmaceuticals, and chemicals.
Besides older malware like WannaCry and NotPetya, newer Windows vulnerabilities like BlueKeep and DejaBlue continue to be discovered in old Windows systems, said Phil Neray, vice president of industrial cybersecurity for CyberX. These can give attackers complete control over a system.
“One of the recently discovered vulnerabilities was similar to the one used in Stuxnet and involved LNK file extension functionality in Microsoft,” he said. “This gives anyone who plugs in a USB drive — often used for updating Windows systems — complete control over those machines. This could be an attacker or just a non-malicious contractor performing maintenance with a USB that inadvertently contains malware.”
Although the standard advice is upgrading to the latest version, this isn’t always practicable in OT environments. For one thing, new vulnerabilities in multiple Windows operating systems, including supported versions, continue to be discovered.
Recommended
Blog: Data Breaches in the Cloud
Last month, for example, the National Security Agency found it necessary to inform Microsoft, in public, that “Windows 10 Has a Security Flaw So Severe the NSA Disclosed It,” as Wired’s headline put it. That critical spoofing vulnerability in Windows 10 clients and 2016/2019 servers is in the very software that validates certificates of trust. It could be used to fake a certificate for executable malware or to decrypt confidential information.
In industrial OT environments, updating an operating system is much more disruptive than it is even on the IT side. Here, Windows systems are widely used either as workstations for plant personnel monitoring manufacturing processes or as engineering workstations to deploy new or updated code into PLCs. “Once these machines are installed in an industrial environment and the plant is running 24/7, it’s hard to justify upgrading to a new version of Windows: the systems have been tested, they’re all working together, and it would require downtime and a lot of effort to stop everything for these upgrades,” said Neray.
Although major antivirus providers did say they’ll continue to support Windows 7 another two years, this merely delays the problem. In addition to unsupported, unpatched older Windows systems, a lack of antivirus software is another reason why older malware versions are still being encountered. The CyberX report found that two-thirds of ICS/IIoT sites analyzed aren’t automatically updating Windows systems with the latest antivirus definitions.
Antivirus software functions can be incompatible with the real-time systems used in ICS, but some antivirus software and anti-malware software are now approved to run on ICS, said Neray. “Also, application white listing, which can be difficult to manage in a corporate environment, is a great way to protect a Windows system in an industrial environment, where what you install should be strictly controlled.”
The report includes suggestions for mitigating cybersecurity risks in IIoT and ICS environments — a seven-step process based on recommendations from Idaho National Laboratory and the NIST Cybersecurity Framework, both recognized authorities on ICS cybersecurity.
— Ann Thryft writes ‘Cloud Watch’ column for EE Times.