Securing API to Protect Your Car-Key Apps
There are too many ways to hack the API of a car-key app. CriticalBlue has a solution for that...
U.S. Election Integrity Creates Unease
US election infrastructure is antiquated and vulnerable. Can we fix it before the 2020 presidential election?
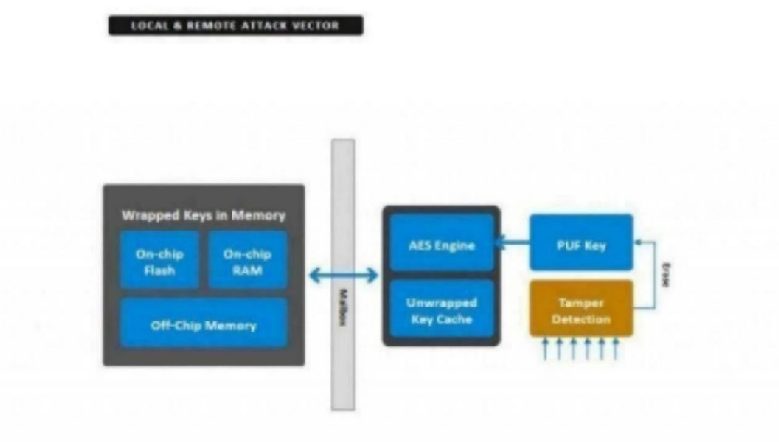
Securing IoT With PUF Technology
Several chip vendors are implementing physically unclonable functions (PUF) to enable security in IoT devices; we looked at two of…
IoT Design Gets Smart and Secure Embedded Solutions
Microchip has launched a range of IoT solutions for rapid prototyping by using cloud connectivity for all integrated microcontroller solutions.
More Apps for ‘Digital’ Car Keys
NXP's “automotive digital key solution” enables smartphones, key fobs and other devices to securely communicate, store, authenticate and share digital…
Huawei: UK Carriers to Be Hit by Clampdown
Strict limits on Huawei gear appears to be an opportunity for Nokia and Ericsson, but they put BT, Vodaphone, and…
Blog: Frailties of LoRaWAN IoT Devices
Probably not very. Simply configuring LoRaWAN security keys is inadequate for preventing IoT devices from being hacked.
Beating Facial Recognition Cheats
Trinamax's technology can identify any material, including live skin. It should be in Qualcomm smartphones in 2021.
Unsupported and Unpatched
Vulnerable to attack, older Windows systems present modern challenges to OT network managers.
Hyperscale is in Need of Security Processors
Without purpose-built security processors, organizations that rely on digital innovation are left with either slowing down to accommodate security limitations,…