IoT: We’re Not Keeping up With Security Threats
Article By : Lou Covey
Building secure IoT devices is not keeping up with the growth of malware. While authentication is a fundamental part of any security paradigm, it doesn’t go far enough.
The semiconductor engineering world is finally realizing that this digital security thing might be more important than just protecting patents. Unfortunately, there are not enough engineers to do something about it and they are building digital technology faster than they are figuring out how to make it secure.
Not a single company exhibiting at DesignCon in Santa Clara highlighted their contributions to designing for security, probably because none of them are. The show organizers did bring in Silicon Valley chip-design luminary Warren Savage to deliver a keynote on the subject. Savage is currently a visiting researcher at the University of Maryland for DARPA programs in the area of intelligence and security and in his one year at the job he has come to believe that Silicon Valley engineers and their companies are completely clueless about how bad the situation is.
“There was definitely an OMG moment shortly into the job where I said, ‘How much do I not know,’” he admitted. “We are designing and building technology and we are not thinking that someone might be figuring out a way to hack it. It has been a complete blind spot for me.”

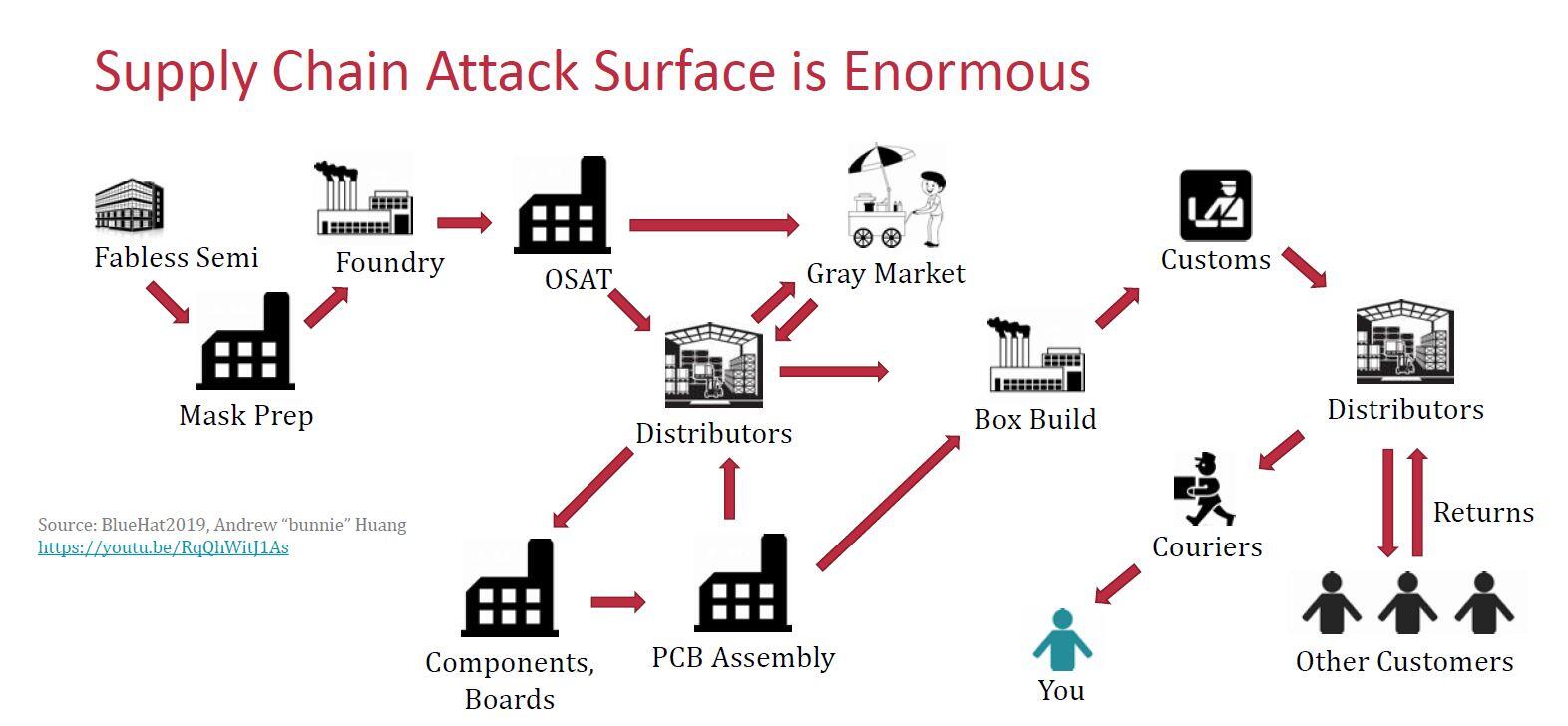
In the keynote, Savage said the biggest security threat to electronics is in the supply chain where there are dozens of potential attack planes. Beginning with a fabless semiconductor company that designs the chip, through mask preparation and foundries, all the way through to the final distribution point. Hardware or software malware can be inserted anywhere along the chain. His slide on this even shows how an end customer can insert malware, both in software and hardware, and return it to a distributor who will send it “refurbished” complete with malware, to another customer looking for a deal.
There are a handful of companies offering partial solutions to the problem, mostly in the area of authentication, most notable is Akamai, Okta, AT&T and Microsoft. All of those solutions are software-based. “We can fix it in software,” has been the mantra of hardware engineers for decades, but for digital security, that concept is failing.
“Software can be copied, reverse engineered and changed,” said Pim Tuyls, CEO of Intrinsic ID, a fast-growing company providing a hardware-based solution to authentication. Tuyls said the only way to truly authenticate data is with a hardware foundation. “All the companies doing it through software can be complementary to our technology, but they don’t really compete with what we do. If you do your security properly in hardware you reduce the problems of malware drastically and you have a stronger foundation to build security into a system.”
The Intrinsic ID technology can authenticate a user entering a data system and can block an unauthorized user trying to insert malware. To date, the technology is being used in more than 200 million devices: credit/debit cards in Asia and in FPGAs for military and government systems. That customer base has grown four-fold in the past year. There is, however, a problem. The number of devices going into service is growing faster than those using Intrinsic ID technology.
According to Gartner, by the end of 2020, there will be 5 billion industrial IoT devices in use and by the end of 2025, 75 billion. Building secure IoT devices is not keeping up with the growth of malware. And while authentication is a fundamental part of any security paradigm, it doesn’t go far enough.

Axel Kloth, CTO of the “smart firewall” startup Axiado Corporation uses the analogy of snail mail.
“Say you receive an envelope and on that envelope is your name and address, a return name and address and a postmark,” he explained. “You can authenticate the recipient with surety. If you know the person on the return address you might know who isn’t it, and the postmark gives you some idea that the government has properly delivered it. But you do not know if the envelope contains a letter or anthrax powder. If you cannot authenticate each part of the delivery mechanism you don’t have security.”
On the technical side, Kloth and Savage pointed out that malware-infected USB devices can easily bypass most security protections.
Savage, in his keynote, stated that at least one engineer at DesignCon was walking around with malware on a thumb drive. Multiple studies going back to 2016 have shown that up to half the people who find a USB drive on the ground will later use it in their own computer, potentially infecting it with malware.
“If you have a VPN setup between your branch office and your headquarters, that’s all fine and dandy, but what happens if someone plugs in an infected USB stick at a branch office?” Kloth asked. “It will first make itself at home in the LAN and then migrate through the secure tunnel to headquarters. So even if your device has authentication, it doesn’t protect the network.”
Both Kloth and Savage advocate for industry-wide adoption of a “design for security” paradigm that goes beyond just securing individual devices and beyond patching software. That’s the core reason for Savage’s work at the University of Maryland and Axiado’s product development.
“Unless you can secure the entire network, you have to assume that nothing is secure,” Kloth stated.
Savage said that since 2012, those that understand security have known there is no safe hardware. He said every major university he knows of, including the University of Maryland, has research programs focused on breaking security protections. “The only answer is in raising the cost of attacks to the point that they are no longer feasible.”
Kloth said his company is working on just such a solution that will provide an added measure of protection for both external and internal intrusions. The collection of products will begin being introduced this year and may provide the first holistic approach to network security.
In the meantime, the engineering community needs a real wakeup call to start putting security to the forefront of product design.
The full interviews with Tulys and Kloth are available on my Crucial Tech podcast. Your questions and comments are always welcome.