Securing API to Protect Your Car-Key Apps
There are too many ways to hack the API of a car-key app. CriticalBlue has a solution for that...
U.S. Election Integrity Creates Unease
US election infrastructure is antiquated and vulnerable. Can we fix it before the 2020 presidential election?
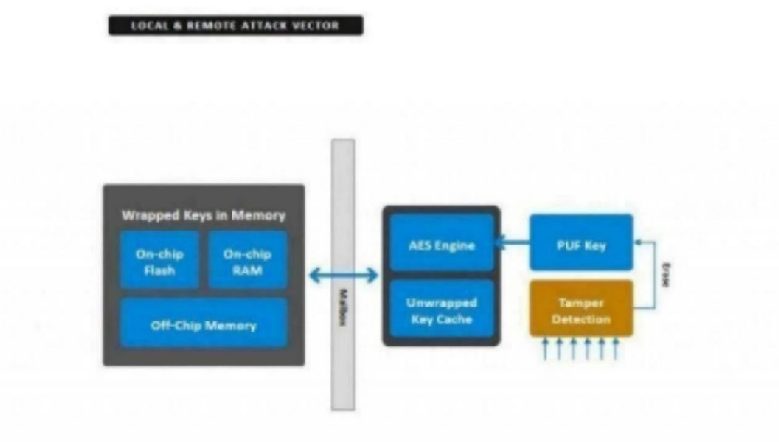
Securing IoT With PUF Technology
Several chip vendors are implementing physically unclonable functions (PUF) to enable security in IoT devices; we looked at two of…
More Apps for ‘Digital’ Car Keys
NXP's “automotive digital key solution” enables smartphones, key fobs and other devices to securely communicate, store, authenticate and share digital…
IoT: We’re Not Keeping up With Security Threats
Building secure IoT devices is not keeping up with the growth of malware. While authentication is a fundamental part of…
Blog: Data Breaches in the Cloud
As data processing, storage, data management and data analytics of IoT/IIoT devices are shifted to the cloud, the need to…
Multi-Finger Authentication for Smartphones
This one- to four-finger authentication capability aims to strengthen security for mobile banking and payments, personal health monitoring, and remote…
Medical Devices Need for Security
Hacking is a perpetual fear, but there's a more prosaic need for safety: preventing device counterfeiting.
Passwords: The Weak Link in Your IoT Network
Poland-based Cyberus Labs is doing something about the problem with passwords.
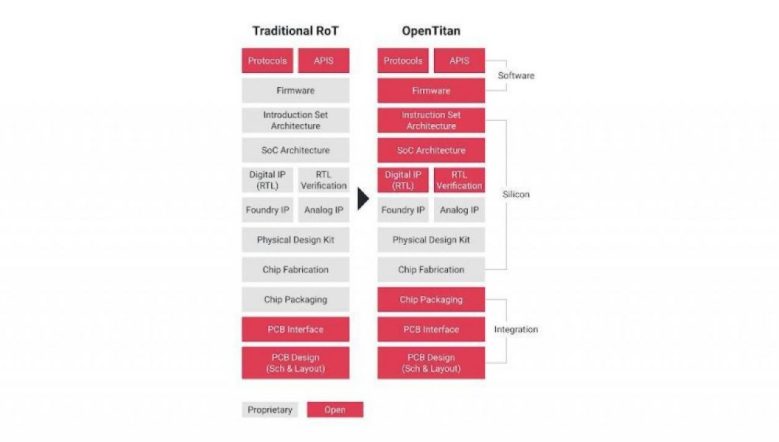
Google Announce Open Source Silicon Root of Trust Project
'Blind trust is no longer necessary', says Google head, as open source silicon root of trust project launches.